February 6, 2015 by Jeroen Arnoldus
Detect Private Calls in iOS App Code

Apple requires that apps only use the public API’s provided by iOS. This tutorial describes how you can list the outbound calls and dependencies of your app and how you can verify they are allowed. Especially, when you are using third party libraries, disallowed dependencies can be created. Manually reviewing these libraries can be very time consuming, and is at least not the aim of using libraries.
1. Locate the App binary
First, create an archive of you app via the Product menu in Xcode. The binary is located in a xcarchive file. These files are stored in:
- $home/Library/Developer/Xcode/Archives/<date>/<appname><datetime>.xcarchive/
Open a Terminal and change directory to this path. The app is located in:
- Products/Applications/<appname>.app
The binary is located in the root of the app directory and its name is <appname>
2. Library Dependencies
The linked libraries can be listed using otool. The command is otool -L <binary>. An example:
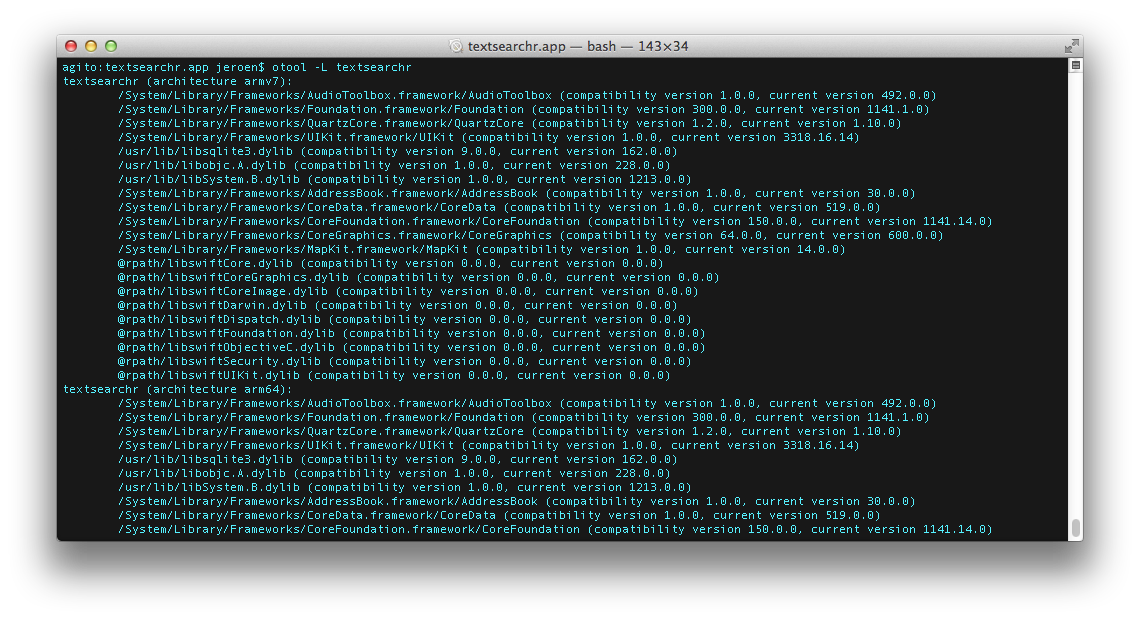
This list can be scanned for libraries which should not be linked, like the obvious IOKit and WebKit library.
3. Linked Symbols
The list of linked symbols can be obtained using the nm -u command. The output will look like:
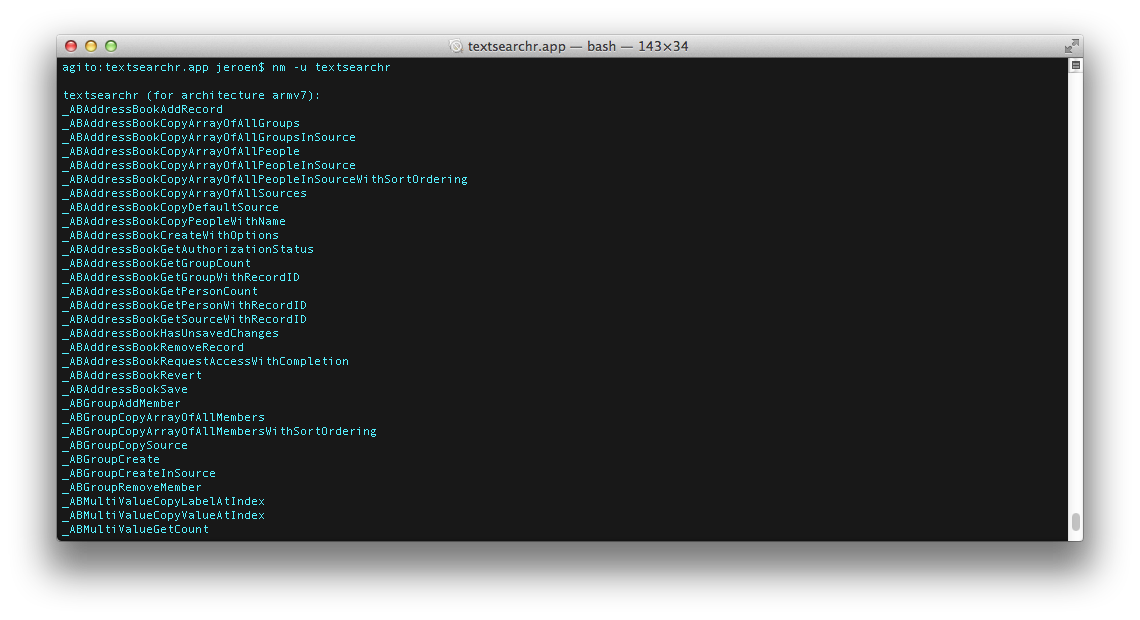
You can use this list to detect:
- Undocumented C functions;
- Private Objective-C classes;
- Ivars
4. What’s next?
Unfortunately, Apple is not providing a list of forbidden symbols. You may search Apple’s documents for every referred symbol to check if it is documented.